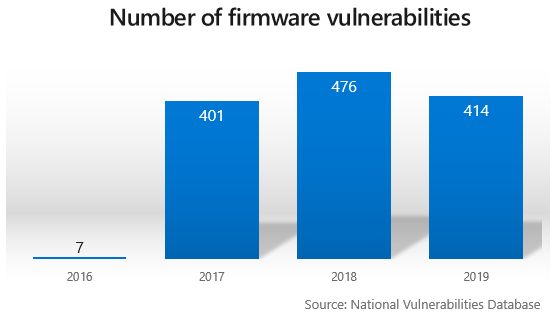
As recently as 2016, firmware vulnerabilities weren't being sought out and found very often. But starting in 2017, one or more has been discovered pretty much every day. (credit: Microsoft)
Microsoft on Tuesday announced a new hardware security initiative, dubbed Secured-core PC. The short version of what "Secured-core PC" really means is a defense against attacks at the firmware layer.
Although actual firmware-based attacks have been relatively uncommon in the field so far, they represent a particularly nasty avenue of exploitation for an advanced, persistent attacker. Once a machine's firmware is compromised, the exploit is persistent across reboots, operating-system re-installations, and even full hard drive replacement.
As operating systems themselves become more secure and difficult to compromise and keep compromised, the value of pivoting from a shell to the firmware layer in order to enhance persistence also increases. Even detection of compromised firmware is problematic, since Windows Defender and other antivirus applications run at the operating-system level and don't necessarily have direct access to the firmware.
Read 10 remaining paragraphs | Comments
https://cdn.arstechnica.net/wp-content/uploads/2019/10/fig1-number-of-vulnerabilities.png
Comments
Post a Comment